近期在使用 Docker 登录自建 Gitea 镜像仓库时,遇到以下错误:Error response from daemon: Get "https://*.com/v2/": remote error: tls: handshake failure常见原因排查(已排除)根据搜索资料和 AI 建议,常见原因包括:证书链不完整(最常见):服务器证书缺少中间 CA 证书自签...
在 PHP 开发中,我们可能会遇到需要修改第三方 Composer 包的情况。直接修改 vendor 目录下的文件虽然简单,但会导致后续 composer update 时覆盖修改。本文分享一种优雅的解决方案——为 Composer 包制作补丁,让你的修改持久有效,同时保持项目可维护性。为什么需要打补丁?当第三方库存在 bug 或缺少功能,但作者尚未修复时,直接修改 vendor 目录会带来...
1. 限流:场景:餐厅领班实时监测大厅入座率,当达到预设承载阈值(80%餐台占用)时,启用排队叫号系统,将新到顾客引导至等候区有序排队。 解析:通过滑动时间窗口算法动态评估系统负载,采用令牌桶机制控制请求准入速率,防止突发流量压垮后端服务。2. 降级:场景:厨房智能调度系统监测到当前订单响应时间超过SLA阈值(30分钟),自动启用应急方案,将非招牌菜系切换为 #预制菜品#,确保核心套餐的出品...
在使用 Docker 构建 PHP 镜像时,我们通常会选择一个官方的 PHP 镜像作为基础镜像,然后在其上安装我们需要的扩展和工具。例如,我们可以使用以下命令来构建一个 PHP 镜像:FROM php:8.4-fpm
RUN apt-get update && apt-get install -y \
libfreetype6-dev \
libjpeg62-...
一、核心问题分析在传统PHP项目架构中(如 WordPress、Discuz!、Typecho 等系统),普遍存在以下安全隐患:文件暴露风险所有PHP文件默认部署在Web根目录非执行文件(配置文件、日志文件)可直接访问版本控制目录(.git/.svn)可能包含敏感信息容器化部署隐患构建过程默认包含全部项目文件开发调试文件(.env)可能泄露CI/CD凭证可能通过配置文件意外打包二、典型漏洞案...
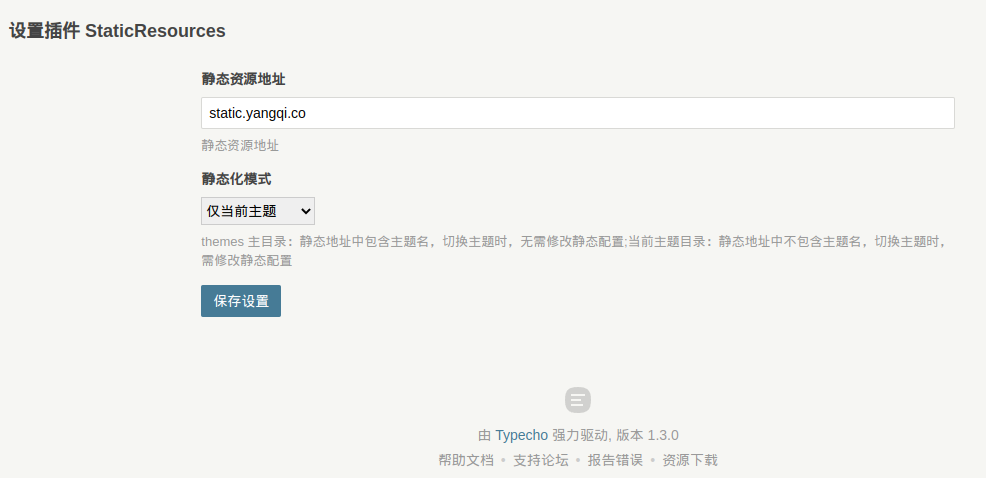
通过实施动静分离架构,将静态资源(如图片、脚本、样式表等)部署至独立二级域名,并整合第三方CDN全球加速服务及云对象存储方案,可显著优化网站性能指标。此策略可同时实现:利用浏览器多域名并发机制提升资源加载效率;通过CDN边缘节点缓存降低网络延迟,改善用户访问体验;云存储服务弹性扩展能力有效降低服务器带宽压力和运维成本。从SEO维度考量,独立资源域名可规避主域Cookie污染,配合CDN智能调...
在 YAML 配置设计中,针对"列表项存在基础形态和扩展形态"的常见场景,我们提供三种结构化方案及其处理逻辑:方案一:全量映射格式(显式冗余)ext:
- name: bcmath
option: [] # 显式声明空列表
- name: curl
option: []
- name: gd
option:
- with-freetype
...
在网络上,我们可以找到免费申请 Azure MySQL 的教程。按照这些教程成功开通后,数据库会被分配一个公网 IP,不过其安全性仅靠防火墙规则来约束。但免费版的 Azure 虚拟机所获取的是动态公网 IP,这让数据库防火墙规则的设置陷入了两难境地:若不设置任何规则,将数据库完全开放,那就只能依靠 MySQL 的账号密码来保障安全。若允许所有 Azure 服务器访问,虽能避免因 IP 变动带...
背景痛点在虚拟化运维中,我们经常遇到这样的场景:反复修改 PVE(Proxmox Virtual Environment)虚拟机配置后,最终发现原始版本才是最优解。这种版本回滚需求在 IT 运维领域尤为常见,而 Git 的版本控制能力正是解决此类问题的利器。恰好,我本地就自建有一套 Gitea 系统。而 Gitea 的 actions 工作流也支持自动化操作。于是就有了这个实现:实施步骤1....
Proxmox VE(PVE)的Web管理界面默认使用HTTPS 8006端口,有点强迫症的我就想将它改成标准的 443 端口。传统方案需修改PVE配置,但每次PVE升级后都会失效。本文通过Linux内核级工具IPVS实现流量转发,无需改动PVE系统本身,系统升级后也对其没有影响。IPVS技术简介IPVS(IP Virtual Server)是Linux内核内置的传输层负载均衡器,常用于构建...